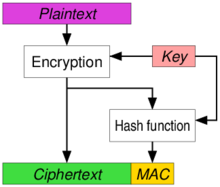
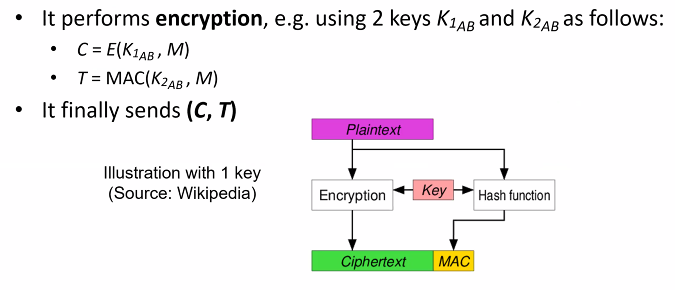
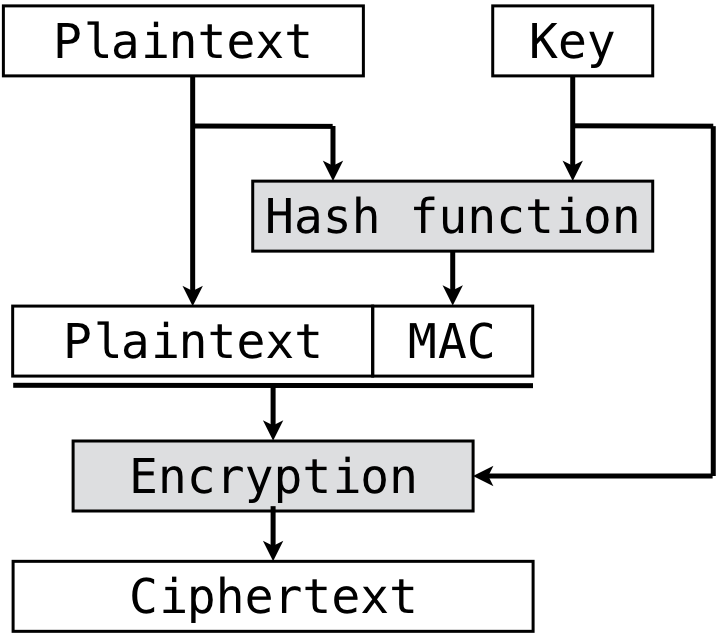
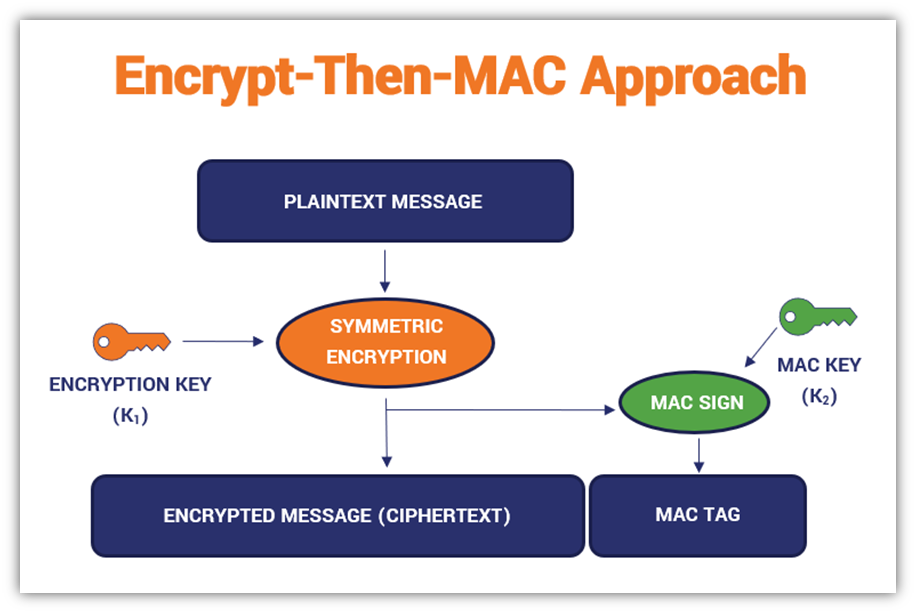
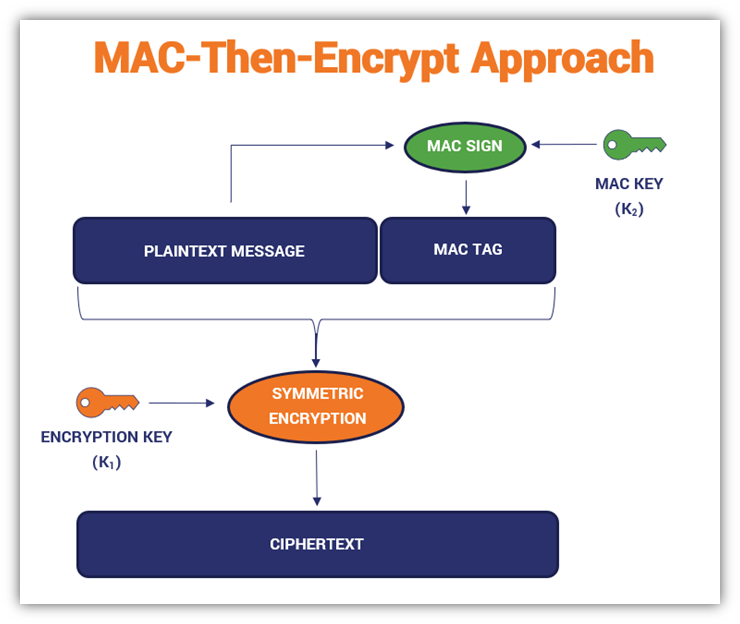
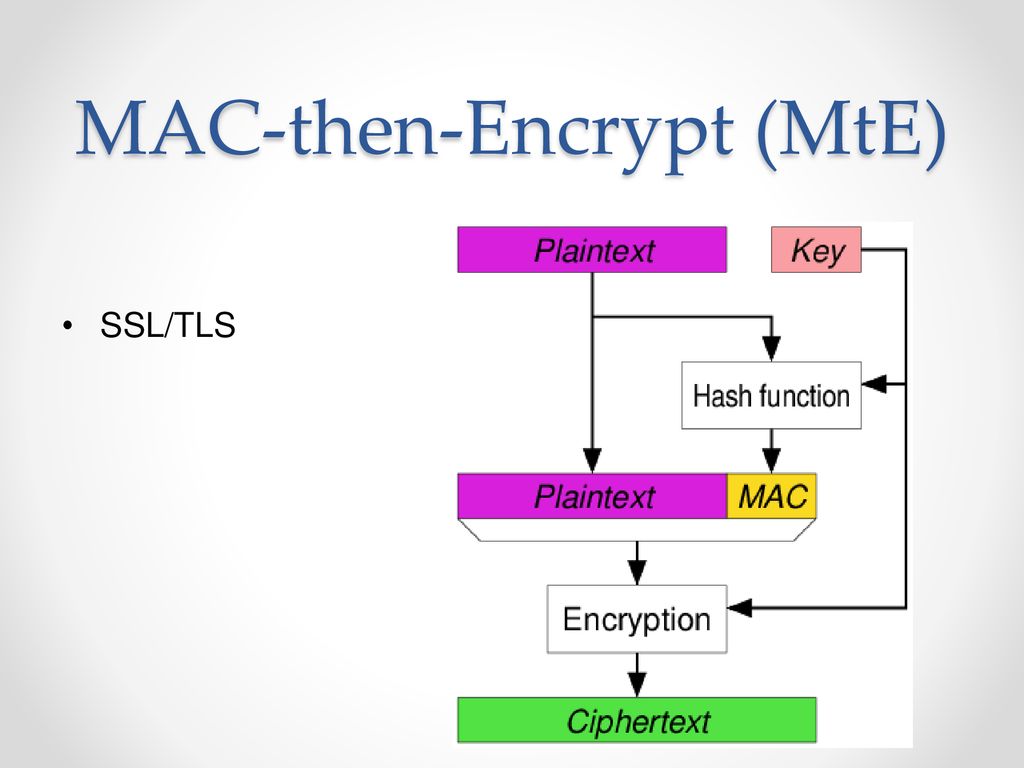
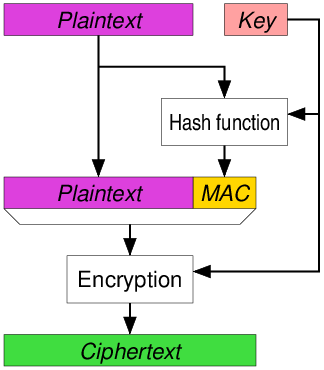
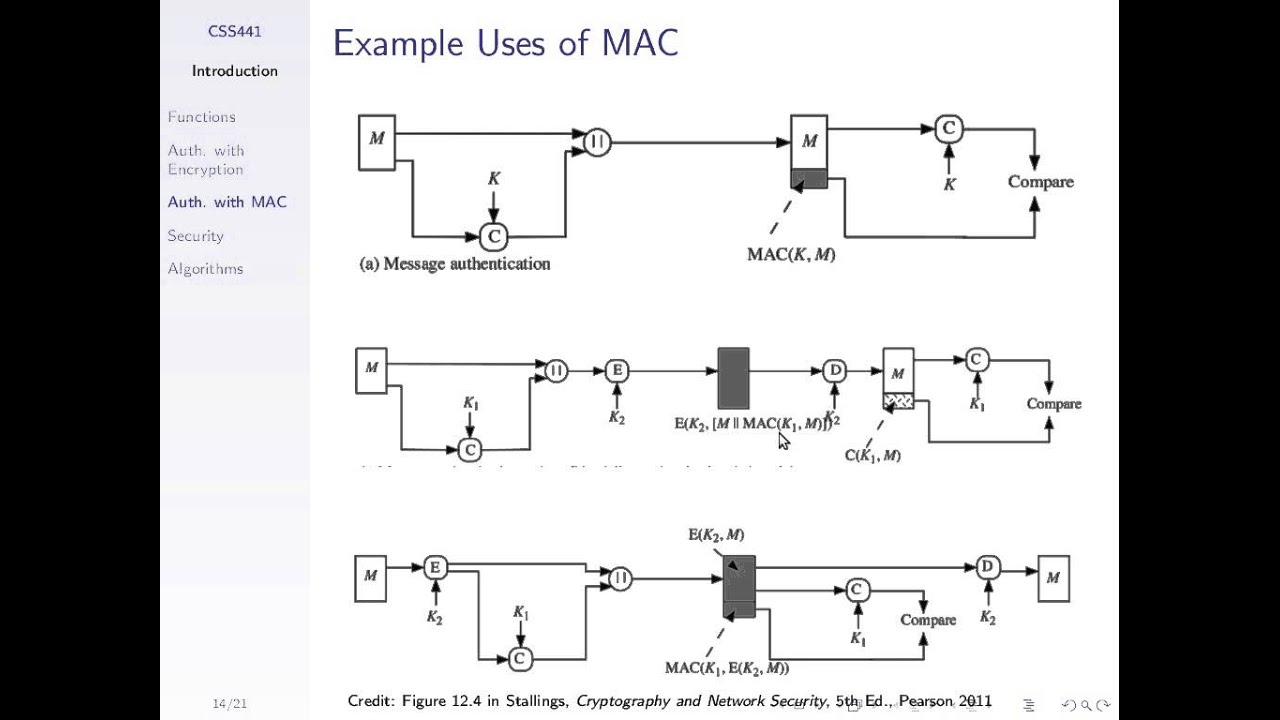
authenticated encryption - Why is a one-time MAC secure for MAC-then-encrypt with randomized-CTR but not randomized-CBC? - Cryptography Stack Exchange

hmac - Why do we encrypt then decrypt then encrypt data with different keys? - Cryptography Stack Exchange